A New Era of Opportunity and Complexity
The Middle East, particularly the Gulf Cooperation Council (GCC) region, is undergoing an unprecedented economic and digital transformation. Visionary initiatives like Saudi Vision 2030, UAE Centennial 2071, and Qatar National Vision 2030 are rapidly diversifying economies away from hydrocarbons and creating a vibrant, hyper-connected digital landscape. For multinational corporations and large enterprises, the opportunity for expansion is immense. However, this digital gold rush comes with a complex and high-stakes set of challenges. Navigating this new frontier requires more than just capital investment; it demands a forward-thinking cybersecurity posture led by strategic expertise. For business leaders planning for 2026 and beyond, leveraging Middle East vCISO services is a critical component for sustainable and secure growth.
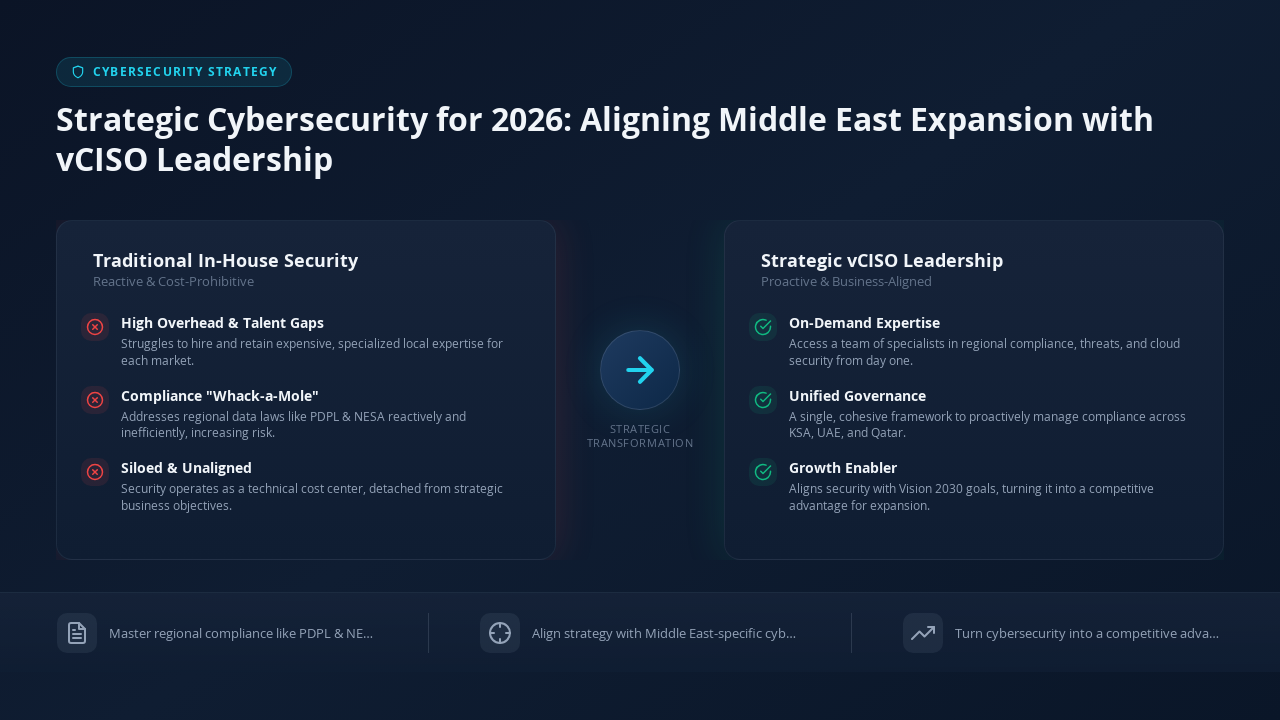
The core pain point for expanding businesses is a widening gap between ambition and security readiness. Companies face a dizzying array of data sovereignty laws, a sophisticated and often state-sponsored threat landscape, and a significant local talent shortage in specialized cybersecurity roles. Attempting to manage these risks with a traditional, in-house security model is often inefficient, costly, and fails to grasp the unique nuances of the region. A Virtual Chief Information Security Officer (vCISO) provides the strategic, on-demand leadership necessary to turn these complex challenges into a competitive advantage.
The GCC’s Unique Cybersecurity Landscape: Beyond the Basics
To succeed in the Middle East, leaders must understand that the cybersecurity environment is fundamentally different from that in Europe or North America. The risks are shaped by unique geopolitical, regulatory, and economic forces.
1. The Rise of Data Sovereignty and Localization
GCC nations are rightfully asserting control over their digital futures. This has resulted in a patchwork of robust data privacy and localization laws that foreign companies must navigate. Key regulations include:
- Qatar’s Law No. 13 of 2016 (PDPPL): One of the first in the region, it sets a high bar for personal data privacy and security.
For a multinational, this means a one-size-fits-all approach to GCC data privacy is doomed to fail. A coherent strategy requires deep, jurisdiction-specific expertise to ensure cybersecurity compliance in the Middle East across all applicable compliance frameworks.
2. A Sophisticated and Motivated Threat Landscape
The region is a prime target for a wide range of threat actors, from cybercriminals to sophisticated state-sponsored groups. Critical infrastructure, including energy, finance, and government services, is under constant threat. Geopolitical tensions often spill over into the digital realm, making businesses operating in the region potential targets for disruptive cyberattacks. An effective security strategy must be threat-informed and tailored to the specific adversaries targeting the region.
3. The Cybersecurity Talent Gap
While GCC governments are investing heavily in education and local talent development, the demand for experienced cybersecurity professionals far outstrips the current supply. For a company expanding into the region, this creates a significant hiring challenge. Finding a single, full-time CISO with proven expertise across the legal, technical, and cultural landscapes of Saudi Arabia, the UAE, and Qatar is nearly impossible and incredibly expensive.
The vCISO: From Security Operator to Strategic Business Enabler
The traditional CISO model, focused on building an internal team from scratch, is ill-suited to the speed and complexity of Middle East expansion. This is where a vCISO service transforms from a tactical cost-saving measure into a strategic necessity. A modern vCISO’s role is not just to manage firewalls, but to align the entire cybersecurity program with the long-term economic goals of the region and the specific growth objectives of the business.
A vCISO acts as a bridge, translating complex technical risks into clear business implications for the board. This strategic guidance is the hallmark of a modern virtual CISO. But What is a vCISO? It’s more than just a consultant; it’s on-demand leadership that integrates directly into your executive team, providing the vision and direction needed to navigate high-stakes environments. They ensure that the company’s Saudi Arabia cybersecurity strategy, for example, is not only compliant with PDPL and NCA regulations but also demonstrates a commitment to being a secure, trusted partner in the kingdom’s Vision 2030 journey.
Key Functions of Middle East vCISO Services for 2026
As businesses look toward 2026, a strategic vCISO partner delivers tangible outcomes that enable growth and build resilience. Their key functions are tailored specifically to the GCC’s unique challenges:
- Optimized Security Investment: Instead of advocating for ever-increasing budgets, a vCISO focuses on ROI. They help determine the most effective use of security funds, often recommending a hybrid model that combines strategic oversight with tactical execution, such as implementing a SOC as a Service to handle 24/7 threat monitoring while they focus on board-level strategy.
Choosing the Right vCISO Partner for GCC Expansion
Not all vCISO providers are created equal. For a successful engagement in the Middle East, business leaders should look for a partner with specific, demonstrable qualities:
- Scalability and Flexibility: The service must be able to scale as your business footprint in the region grows, providing more support as you enter new markets or launch new products.
Conclusion: Secure Growth in a Visionary Region
Expanding into the Middle East in 2026 offers transformative potential, but it demands a cybersecurity strategy that is as ambitious and forward-thinking as the region itself. The complexities of data sovereignty, the sophisticated threat landscape, and the shortage of local talent render traditional security models inadequate. For business leaders, the path to secure and sustainable growth lies in strategic alignment and expert guidance. Engaging Middle East vCISO services provides the essential leadership to navigate regulatory hurdles, manage advanced threats, and, most importantly, position cybersecurity as a core enabler of your long-term success in one of the world’s most dynamic markets.
Get More Security Insights
Join security practitioners who receive our weekly compliance and security newsletter.
Further Reading
Ready to Scale Your vCISO Practice?
See how GetCybr helps MSPs deliver enterprise-grade security services.